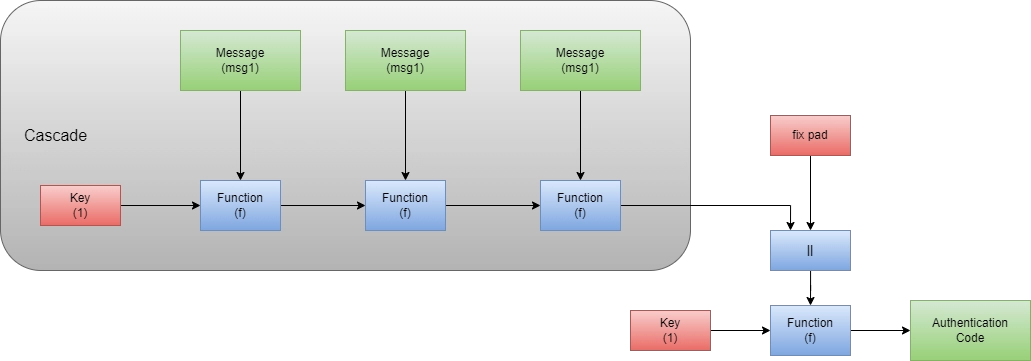
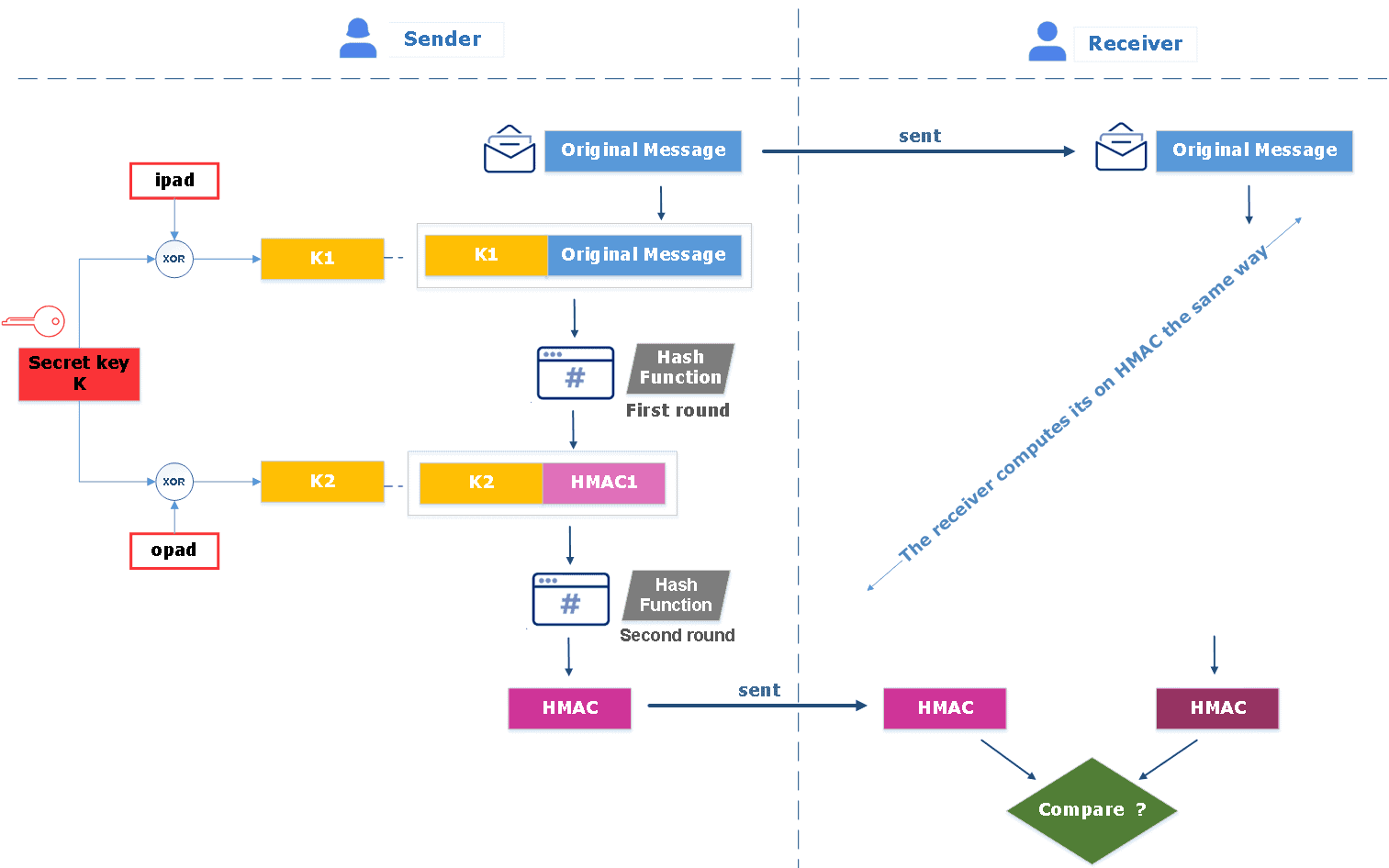
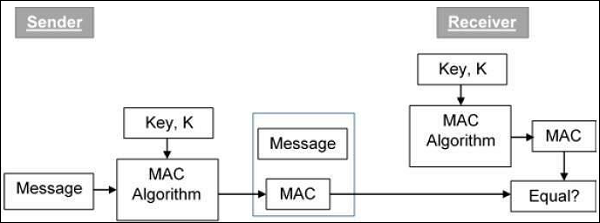
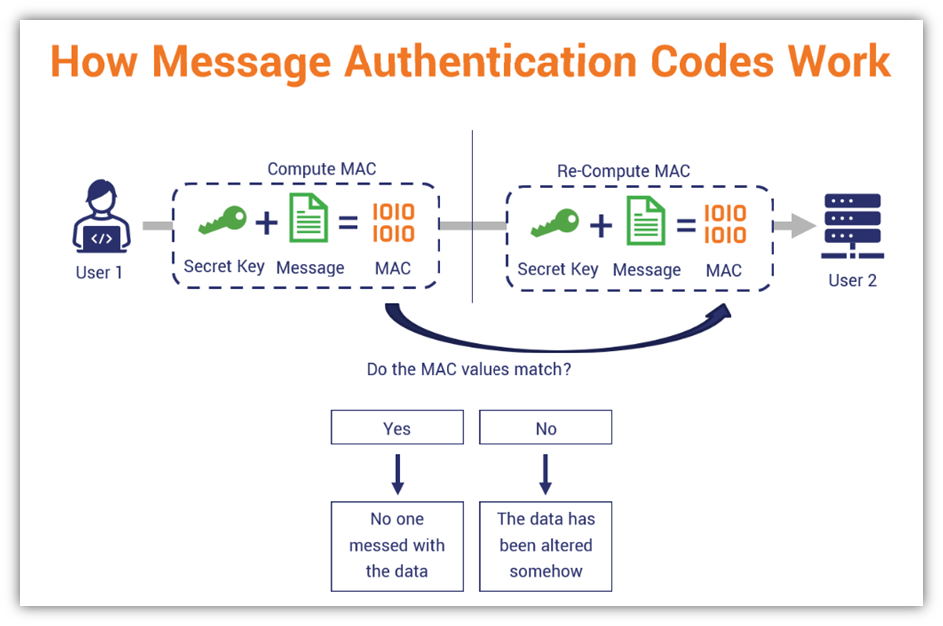
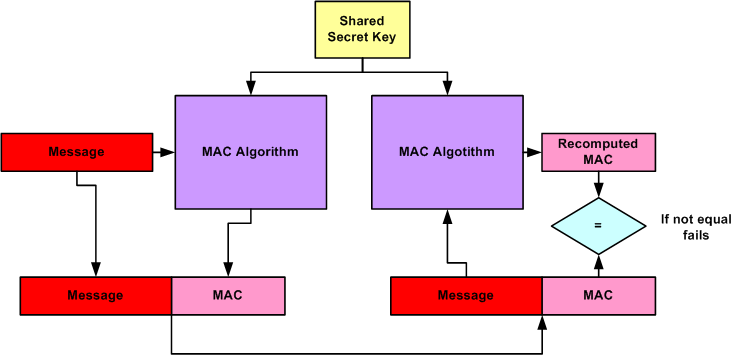
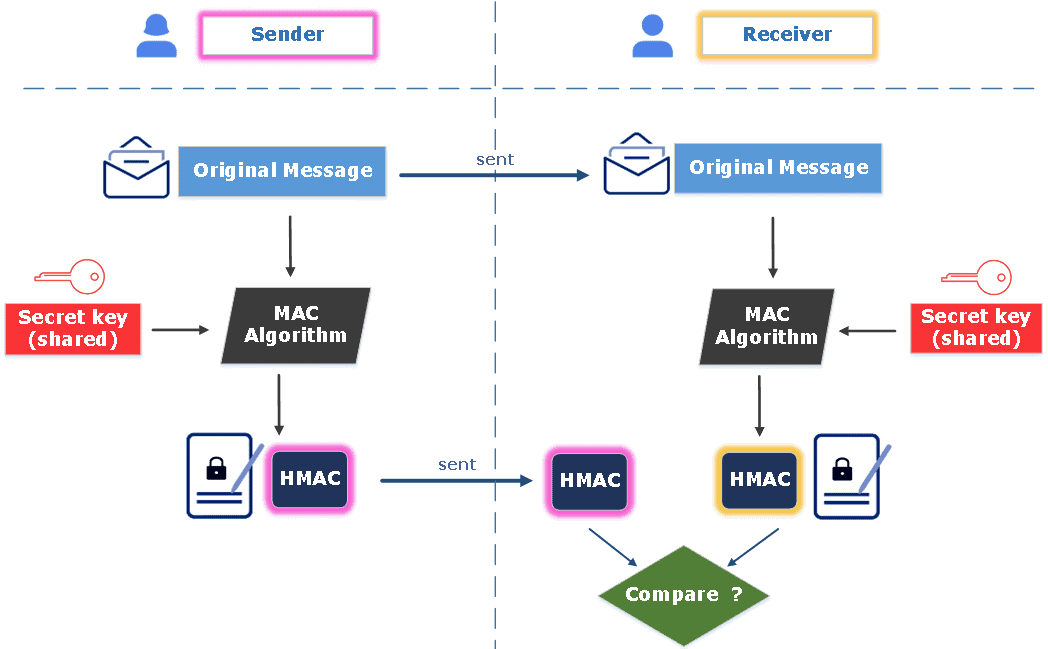
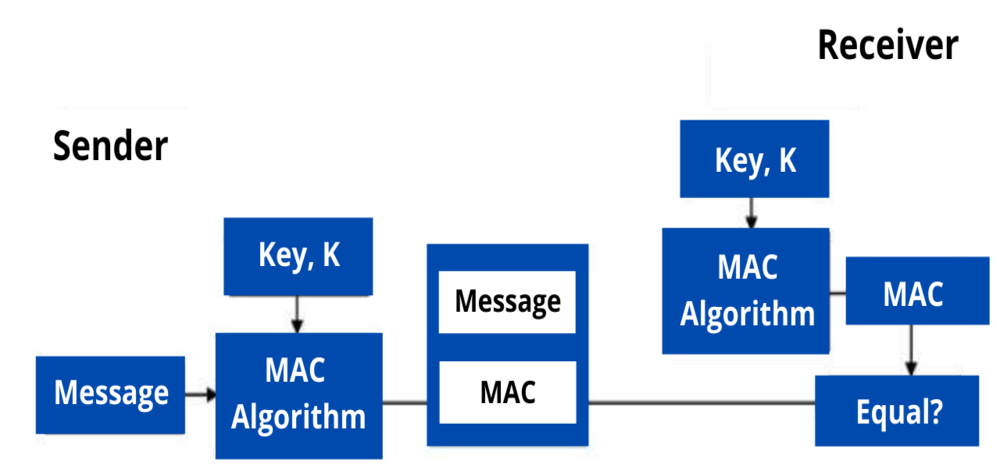
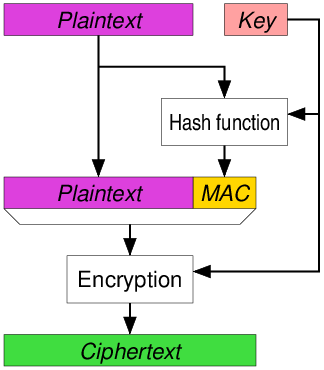
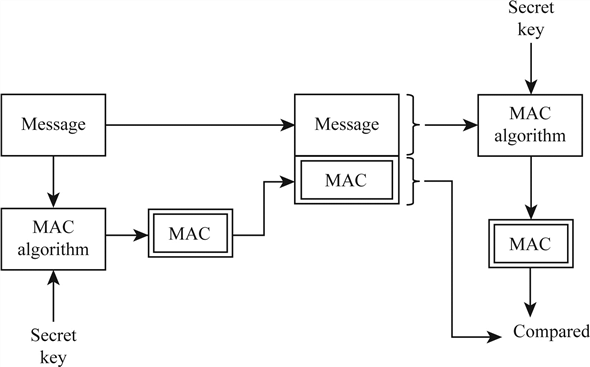
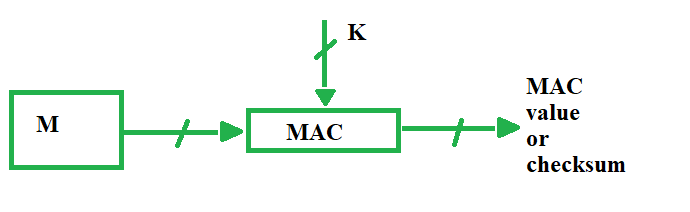
Figure 7. Working of MAC : Review on Network Security and Cryptography : Science and Education Publishing
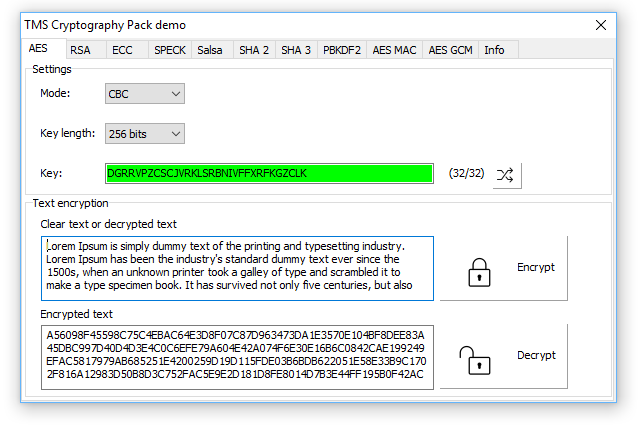
TMS Cryptography Pack Software library that provides various algorithms used to encrypt, sign and hash data.
GitHub - NilFoundation/crypto3-mac: Message authentication codes for =nil; Crypto3 cryptography suite




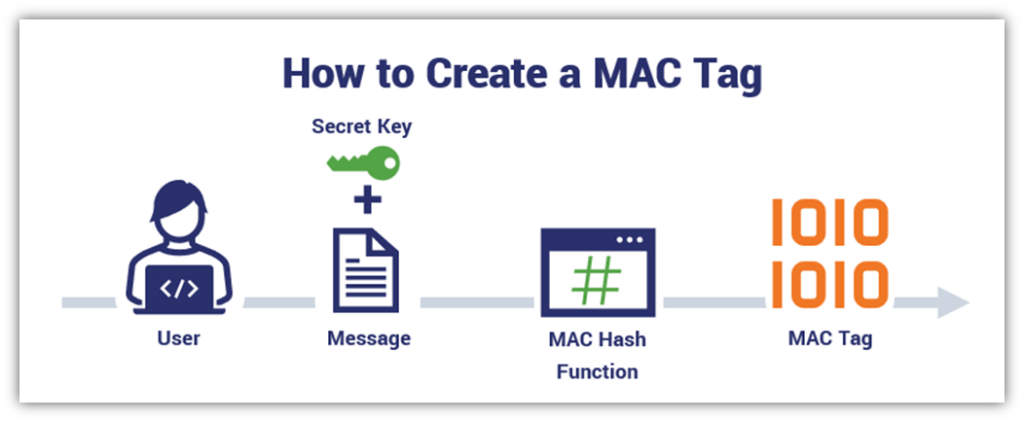
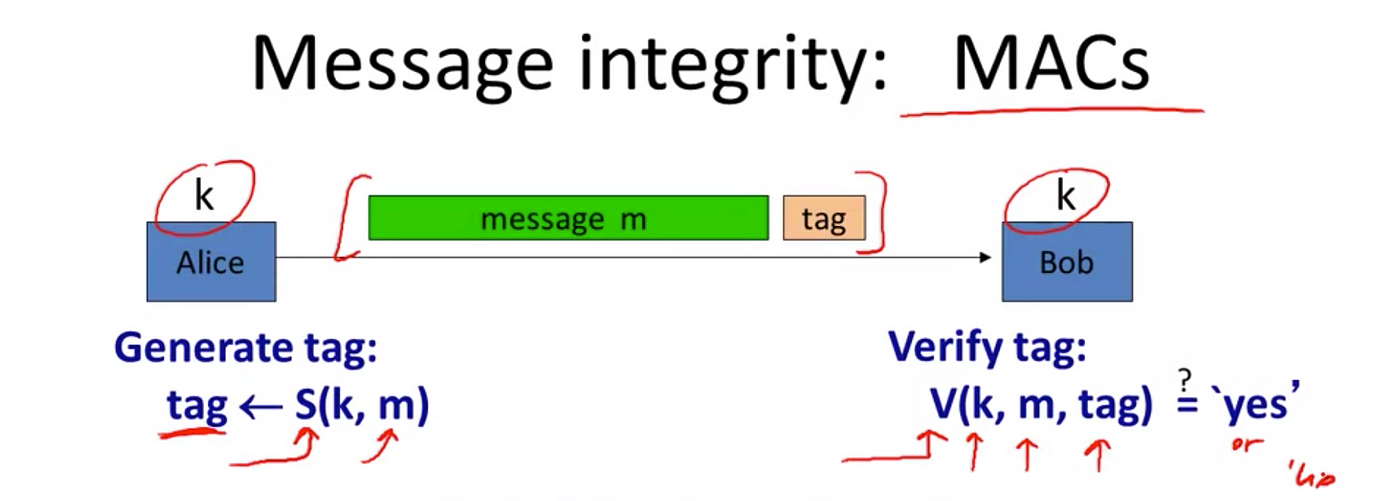
.svg/570px-CBC-MAC_structure_(en).svg.png)