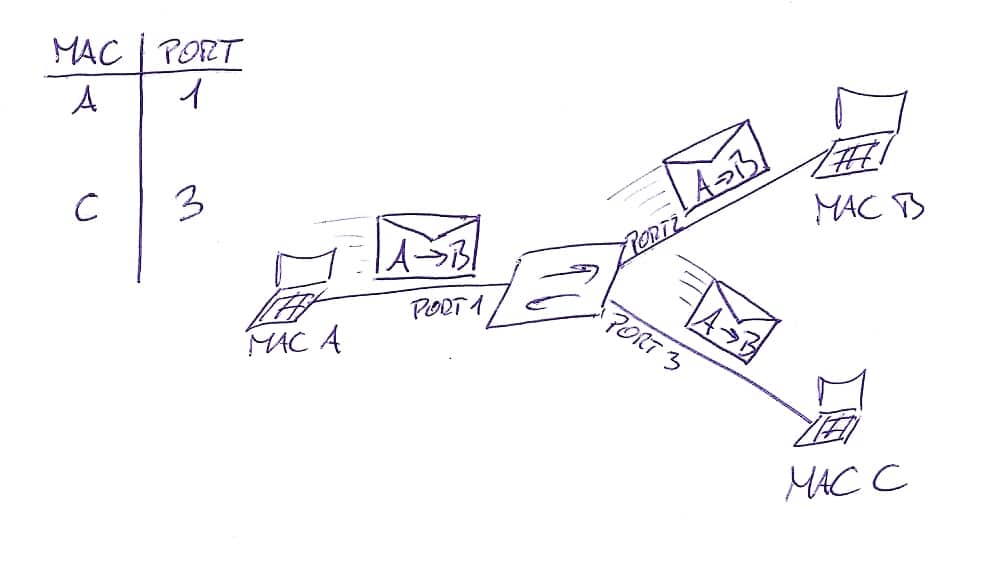
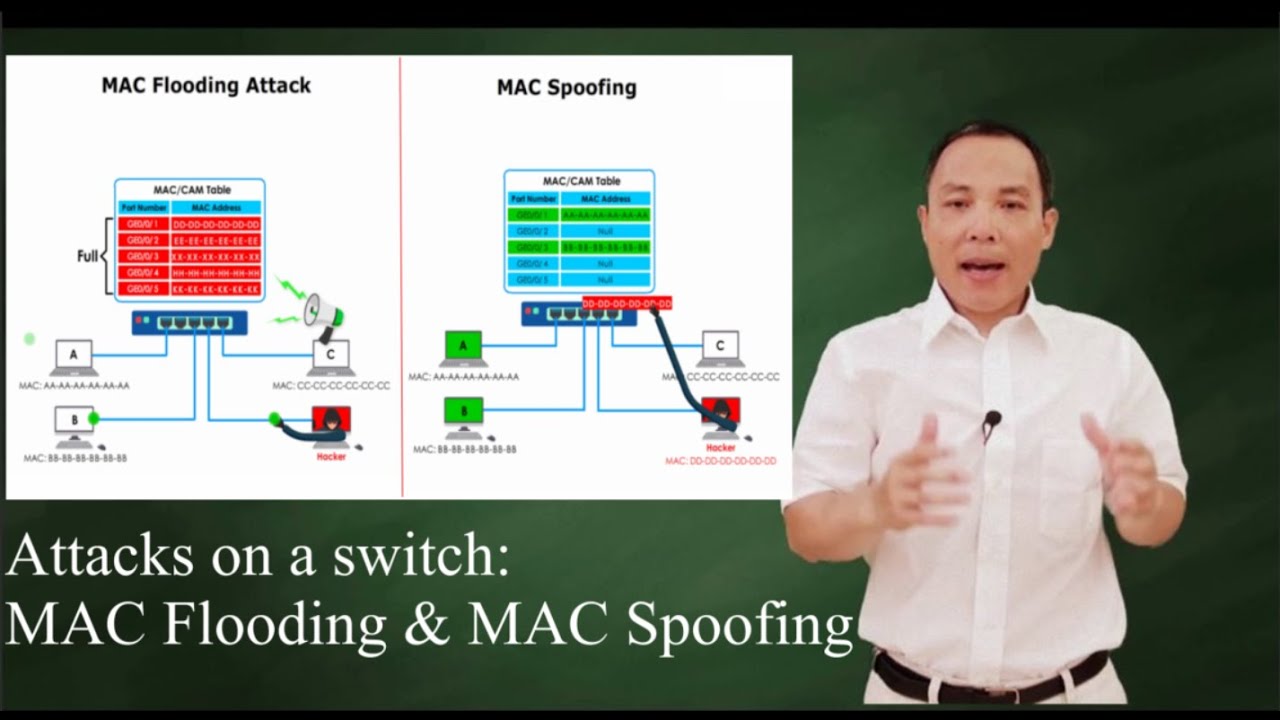
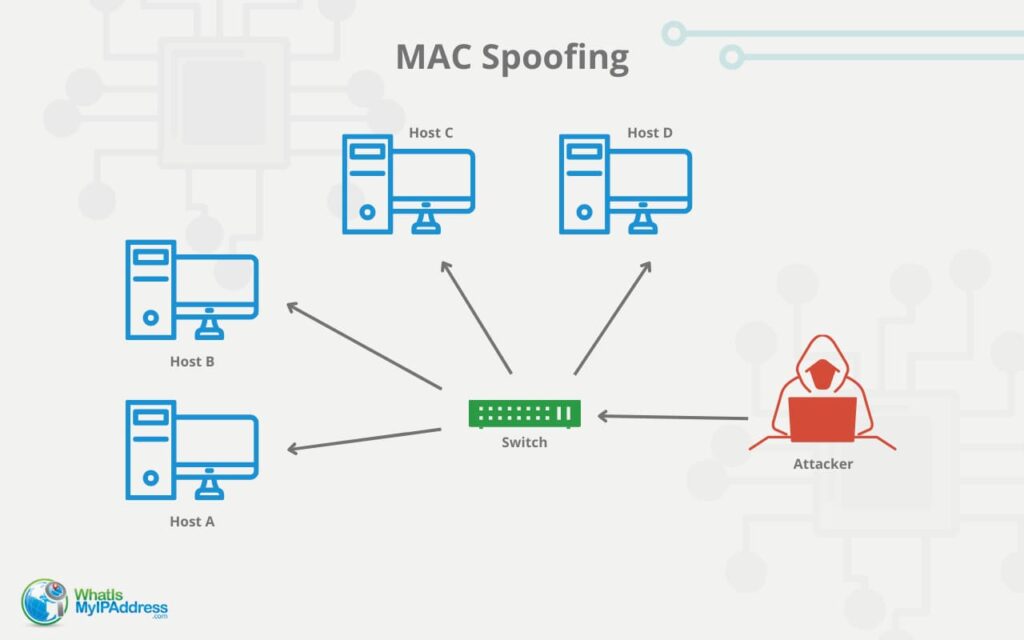
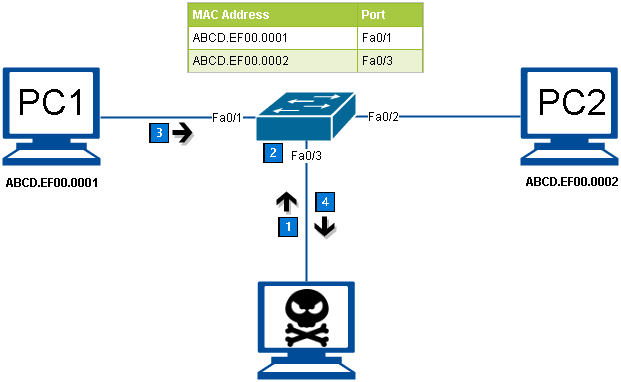
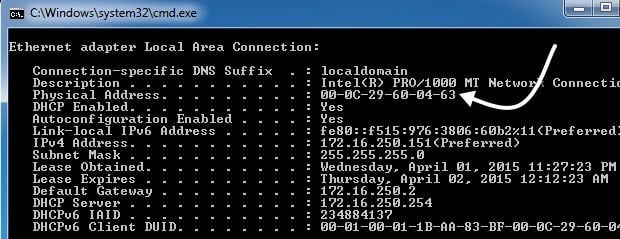
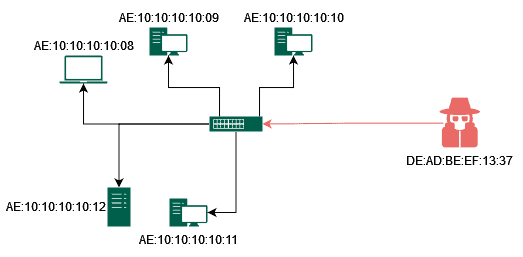
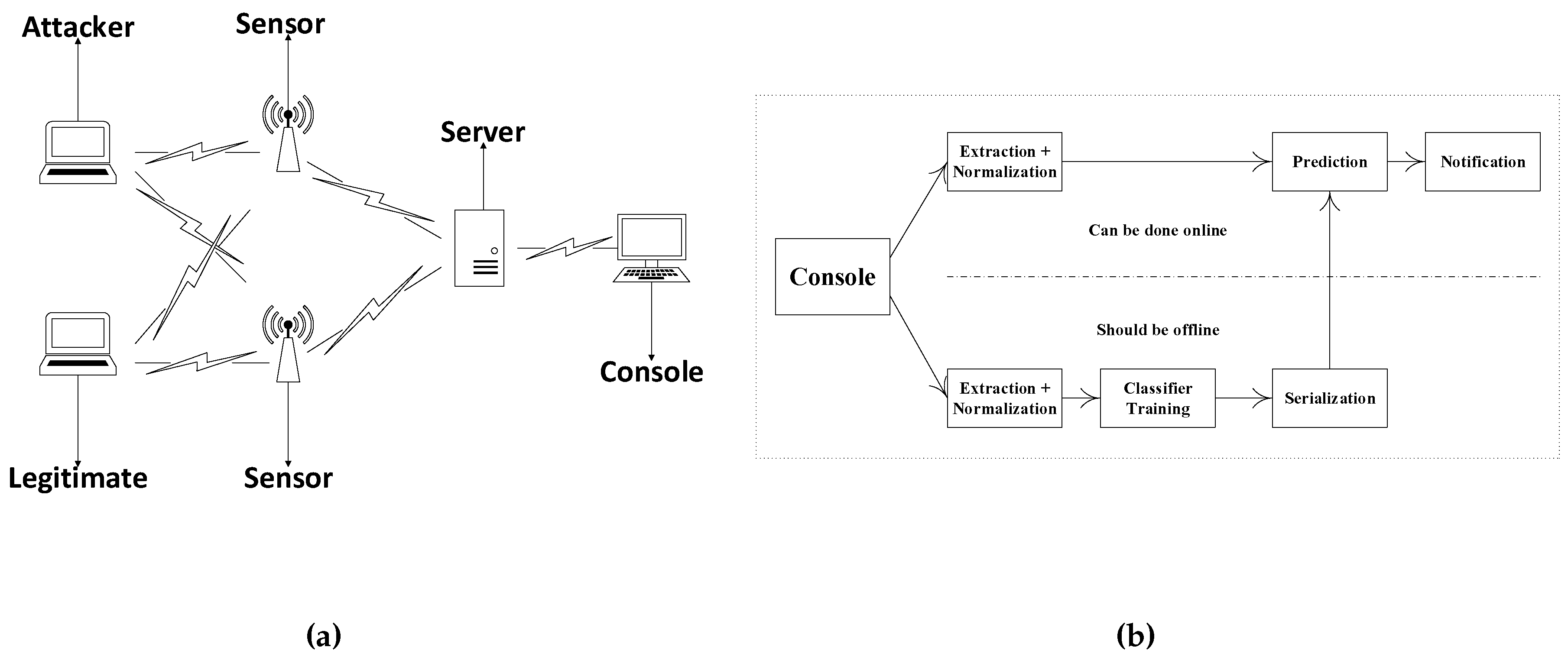
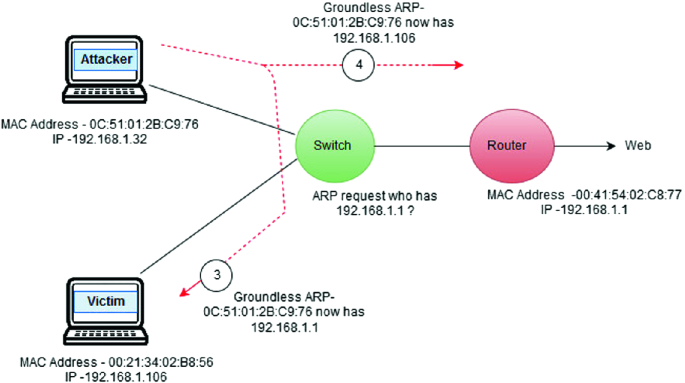
Cyber Crime Control Foundation - What is MAC spoofing? MAC spoofing is a method used to change the factory-assigned Media Access Control (MAC) address of a network interface on a networked device.
Reliable Monitoring Security System to Prevent MAC Spoofing in Ubiquitous Wireless Network | SpringerLink